Cyber threats keep evolving, and perimeter-based defenses weren't built for today's boundaryless environments. That's why more security leaders are adopting a Zero Trust approach. 🛡️ Microsoft's infographic, "The New Shape of Zero Trust," shows how continuous verification, least-privilege access, and AI-powered protection work together to secure every identity, device, and connection. Review the infographic to see how Zero Trust architecture is adapting for the AI era. @Microsoft Security
10 essential insights from the Microsoft Digital Defense Report 2024
Staying informed about trends and predicting potential threats is crucial for developing a cybersecurity strategy that can evolve with shifting cyber dangers. 🛡️ Check out this article from @Microsoft Security for key insights and practical strategies. Feel free to reach out if you need assistance with implementing these approaches.
Microsoft 365 Copilot Customer Stories
AI delivers value when it's embedded where you already work. 🤖 The video, "Microsoft 365 Copilot Customer Stories," shows how organizations are using Copilot to automate routine tasks, surface insights faster, and help employees focus on what matters most. Watch the video to see how you can translate Copilot into productivity gains and business growth. @microsoft-copilot @Microsoft-365
NetApp and 49ers Foundation data analytics education
What happens when data meets hands-on learning? 🤔 For more than 30 years, the 49ers Foundation has supported STEAM education for underserved students. Now, with NetApp, students explore data analytics and technology careers through hands-on learning tied to real game day operations at Levi's Stadium. Watch the customer story video to see how modern data infrastructure supports education and opportunity at scale. @NetApp #AI #GenAI
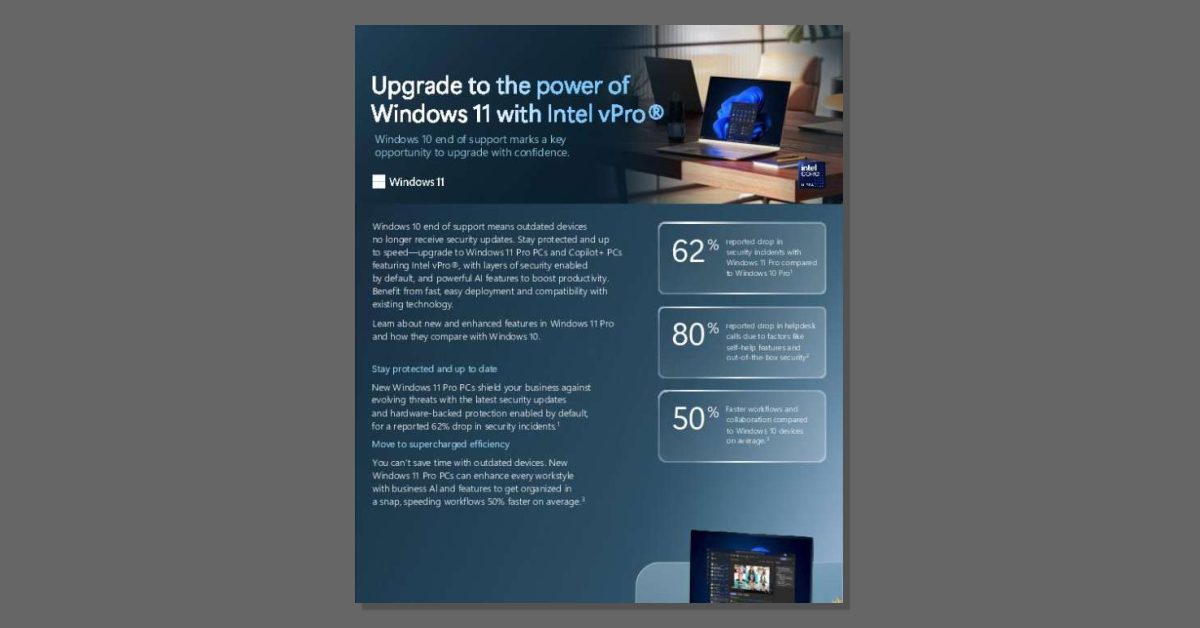
Upgrade to the power of Windows 11 with Intel vPro
⏳ It's time to upgrade. Download the datasheet, "Upgrade to the power of Windows 11 with Intel vPro," for an overview of features in Windows 11 Pro with Intel vPro that reduce security incidents by 62% and speed workflows by 50%. Then, message us to start planning your upgrade with expert support. @Microsoft Windows
The Business Value of Azure VMware Solution
IDC research shows how businesses are achieving measurable results with @Microsoft Azure VMware Solution: ✅ 357% ROI over 3 years ✅ 30% lower infrastructure costs ✅ 91% less unplanned downtime The IDC report, "The Business Value of Azure VMware Solution," details how companies are reducing costs and improving agility by extending VMware environments to the Azure cloud. Download your complimentary copy to see how Azure VMware Solution delivers enterprise-scale efficiency and flexibility.
Amgen builds agent in 6 weeks with Copilot Studio to help accelerate R&D | Microsoft Customer Stories
In a world where every week counts, speed and accuracy can transform possibilities. Amgen developed a tailored R&D agent within six weeks using Microsoft Copilot Studio, highlighting the ability of autonomous agents to simplify intricate research processes and boost innovation. Check out the story to discover how your organization can create custom agents that produce tangible results. @Microsoft 365 @Microsoft Copilot
The Total Economic Impact of Microsoft 365 For Business
In the realm of digital transformation, evidence is key. Small and medium-sized businesses (SMBs) are witnessing a remarkable 223% return on investment with Microsoft 365 for Business, with a payback period of under six months. 💸 Interested in achieving similar results? Download the Forrester TEI report to begin. @Microsoft 365
The New Zero Trust Guide for CISOs
As AI expands both what's possible and what's at risk, you need a more adaptive approach to protecting your people and data. 🤖 View the infographic to see how Zero Trust helps secure identities, data, and devices in an AI-driven world. @Microsoft Security
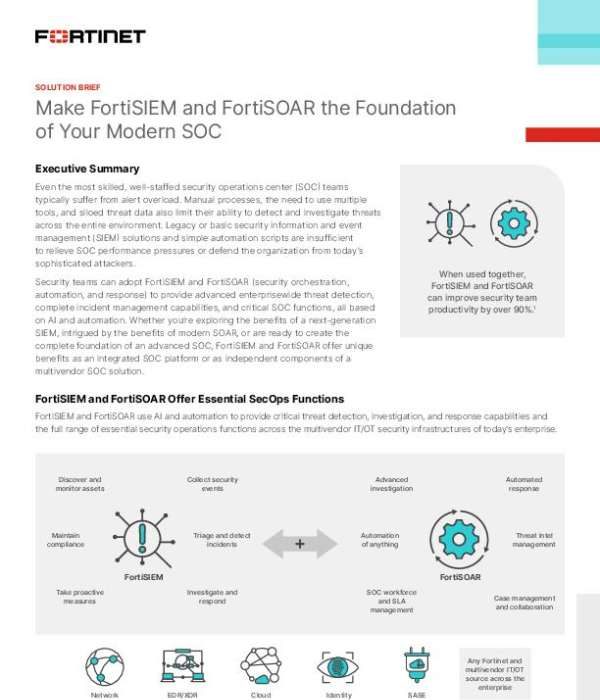
Make FortiSIEM and FortiSOAR the Foundation of Your Modern SOC
Alert fatigue. Siloed tools. Manual workflows. Even the best-staffed SOCs struggle to stay ahead of today's complex threats. The solution brief, "Make FortiSIEM and FortiSOAR the Foundation of Your Modern SOC," describes how Fortinet brings AI, automation, and deep integration together to transform security operations. From GenAI-assisted investigation to 800+ automated playbooks and multivendor threat response capabilities, FortiSIEM and FortiSOAR give your SOC the agility and intelligence it needs. Download the solution brief to discover how a @Fortinet foundation can help your SOC cut response time from hours to minutes.