What is an AI agent, and how can it benefit your business? 🤖 Microsoft 365 Copilot Agents use AI to automate and execute business processes, working alongside or on behalf of people, teams, and entire organizations. Take a look at this infographic to see how agents interact with your data and systems to optimize work, streamline decisions, and enhance productivity. @Microsoft 365 @Microsoft Copilot
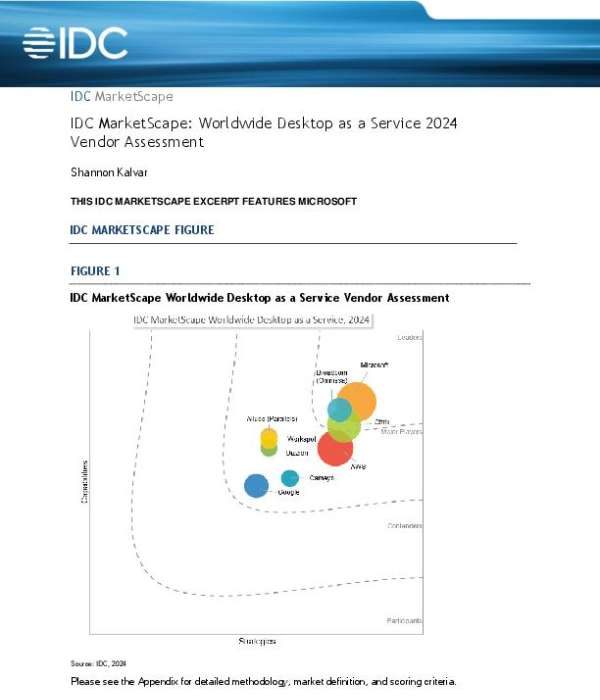
IDC MarketScape: Worldwide Desktop as a Service 2024 Vendor Assessment
What makes a #DaaS solution stand out? 🏆 The IDC MarketScape report has recognized Microsoft #Windows365 as a trusted leader in the market. Learn how it delivers seamless scalability, simplified IT management, and enhanced productivity. Download the report today and message us for a consultation to explore what Windows 365 can do for your organization.
Transitioning from Windows 10: A Strategic Guide
Secure by design. 🔒 Windows 11 Pro PCs with Intel vPro® are secure by design, with protections like secure boot, hardware-based encryption, and identity safeguards enabled right out of the box. The eBook, "Transitioning from Windows 10: A Strategic Guide," walks through the advantages of built-in protection and how it helps organizations move forward without compromise. Download the eBook to see how you can simplify deployment and reduce vulnerabilities, all while improving productivity. @microsoft-windows @microsoftcopilot
Kent County Council can focus more resources on frontline service delivery after deploying Microsoft 365 Copilot | Microsoft Customer Stories
When frontline services face challenges, every available resource becomes crucial. Discover how Kent County Council utilized Microsoft 365 Copilot to reduce administrative tasks, allowing them to dedicate more resources to frontline services. Check out this story to learn how you can attain similar outcomes. @Microsoft 365 @Microsoft Copilot
8 years as a Leader in the Gartner® Magic Quadrant™ for Access Management | Microsoft Security Blog
Identity attacks hit more than 600 million per day, and most still target passwords. 🗝️ Review this analyst report to see why Microsoft was named a Leader again in the Gartner Magic Quadrant for Access Management. Then, message us to discuss how we can help you apply these insights to your identity strategy. @Microsoft Security
Secure employee access in the age of AI
Handling numerous security tools and teams can often introduce more risks than it mitigates. Most organizations acknowledge that enhancing collaboration and consolidating tools can boost both security and efficiency. Download the eBook, "Secure Employee Access in the Age of AI," to discover how integrating identity and network access can enhance security and streamline management. @Microsoft Security
NetApp AIPod Mini with Intel
Find AI solutions that align with your team's needs instead of adapting to them. 💡 Check out the solution brief, "Breaking Through Barriers to AI Success," to discover how @NetApp AIPod Mini with Intel simplifies departmental AI, making it more scalable and budget-friendly.
Microsoft recognized as a Leader in the 2024 Gartner® Magic Quadrant™ for Desktop as a Service for the second year in a row
Leadership matters. Go with a brand you can trust. 🤝 @Microsoft has named a leader in the DaaS industry — for the second year in a row! Read the blog to see why. Check out this blog to learn why Microsoft continues to lead the way.
The fast track: CSX transforms operations for 23,000-plus employees with Azure and AI | Microsoft Customer Stories
Speed and scale are critical in every industry, and CSX found both by migrating VMware workloads to @Microsoft Azure. 🚄 Read the customer story to see how Azure VMware Solution can help your business transform faster and more strategically.
Streamline Visibility and Improve Threat Response with Fortinet FortiAnalyzer
Overwhelmed by security alerts? With FortiAnalyzer from Fortinet, you can empower your SecOps team to reduce the noise and speed up response. This solution brief breaks down how FortiAnalyzer bridges network and security ops, delivers GenAI-assisted investigations, and consolidates threat intelligence into one unified view. Download the solution brief from @Fortinet for insight on how to streamline workflows and protect more, with less.